Journalism Safety - Policy/Action plan
Below is our policy/action plan that individuals or smaller organisations can use for online safety support.
Online Safety Policy
This document is designed to be adopted by media and journalistic organisations which do not have the resource available for in-house online safety management. It can also be used by freelance journalists and not-for-profit organisations which support journalists.
The wording and guidance in this document is the intellectual property of Rebecca Whittington and is copyrighted to Reach plc and Women in Journalism. Credit must be given if it is reproduced for staff or user access in any digital or print format. This document should not be copied or shared for commercial purposes and the contents should not be repurposed without credit to the source.
The purpose of this policy:
This document offers guidance and a framework to be adopted by employers and organisations with responsibility for journalists who might be at risk of online harm during the course of their work.
The policy includes practical guidance around psychological, digital and physical safety. The document sections include:
Protections against online safety threats
1.1 Protection is the best form of defence
1.2 Basic protections
1.3 Risk assessment
2. Responding to online safety threats
2.1 Assessment grid
2.2 Assessment grid
2.3 Online harm response
1. Protection against online safety threats
1.1 Protection is the best form of defence: Encouraging journalists to consider their digital safety is good practice and reduces the risk of online attack. By putting appropriate protections in place, the damage inflicted by online attacks is significantly minimised and the period of recovery from an attack is shortened.
1.2 Basic protections:
Multi-factor authentication on all professional and personal accounts
High-level privacy settings on personal social media, including on images, location trackers and check-ins, personal information and conversations.
Separation of personal and professional social accounts
Creation of a checklist of personal information an individual is comfortable sharing publicly and applying the list to professional/public-facing information
Using a different name for personal social media
Checking social history to ensure content still aligns with current personal views and ethics and does not reveal personal information
1.3 Risk assessment:
In the case of content production and distribution of topics known or anticipated to cause physical or online safety threat, a risk assessment should be conducted which takes into account the risks and identifies mitigation measures to minimise the threat. This should include assessment of content gathering practice, physical safety risks and identifying how content will be presented and promoted. All persons involved with the process should be considered as part of the risk assessment and outcomes should be communicated to all parties.
2. Responding to online threats:
2.1 Assessment
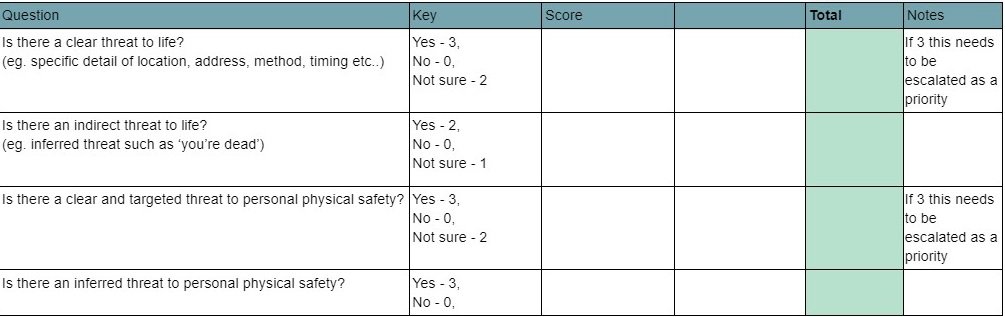
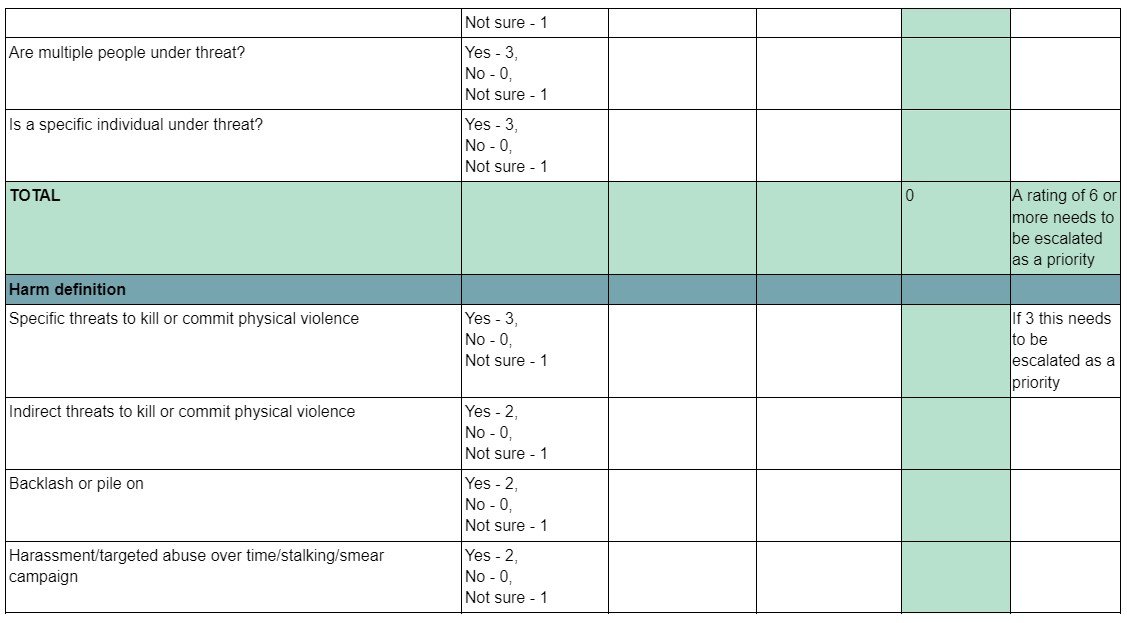
When an online safety incident occurs there are two key elements which must be considered prior to response. These are:
How can the threat be categorised?
How does the individual target feel about the threat?
By establishing these facts, the response to the threat can be managed in order to minimise the impact and extent of the event, while also ensuring the preservation, as much as possible, of the psychological safety of the individual.
2.2 Assessment grid
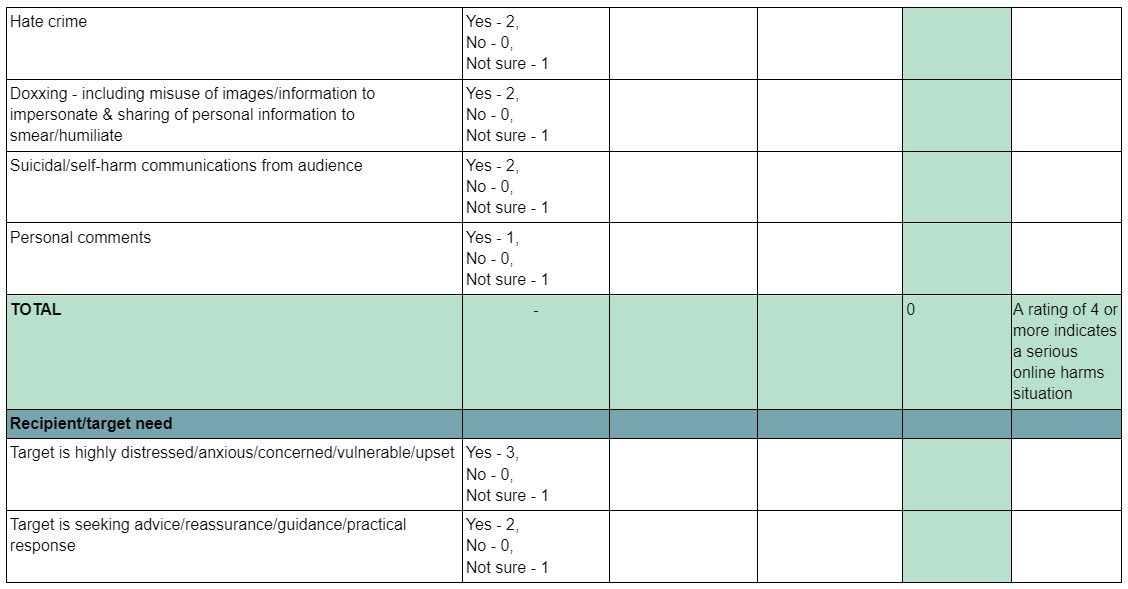
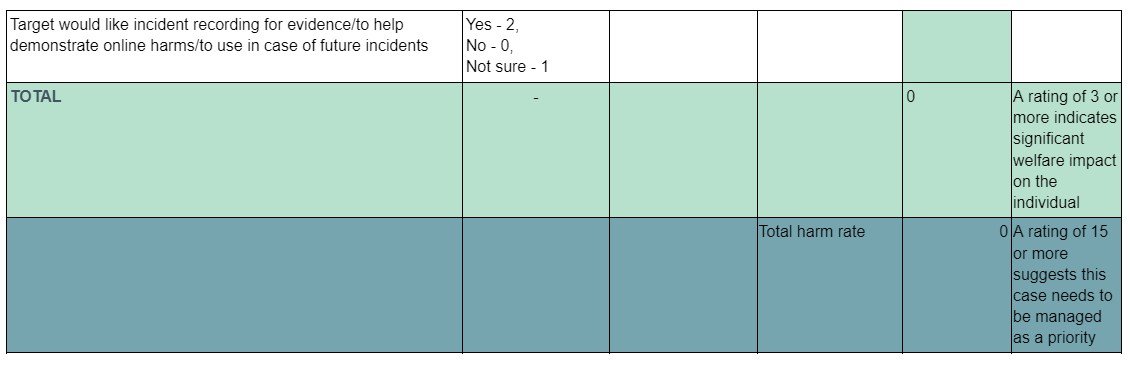
2.3 Online harm response
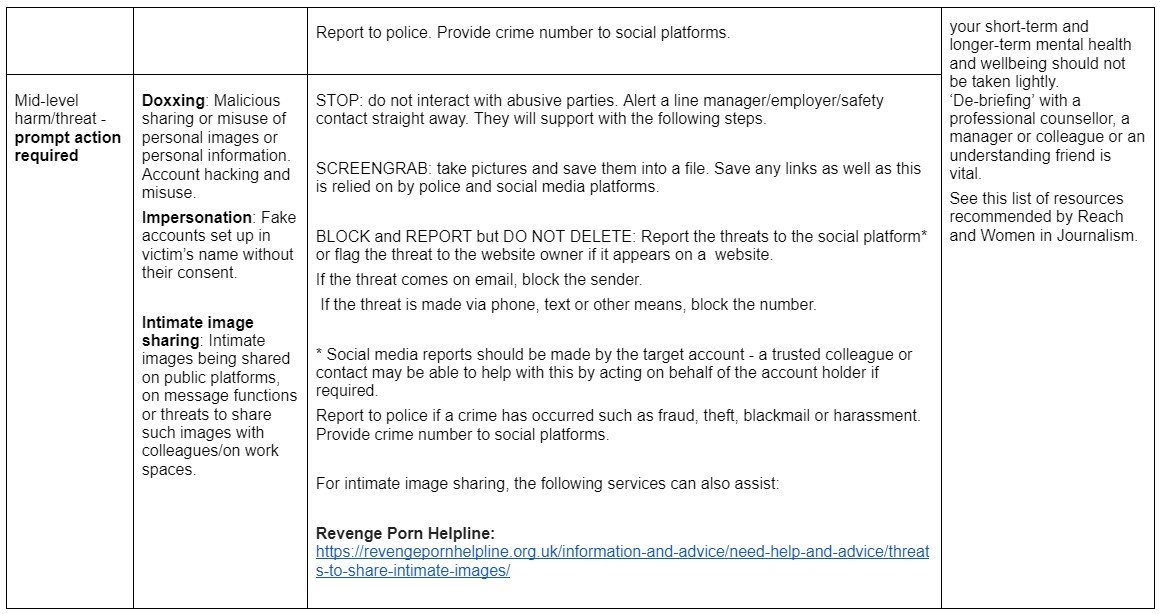
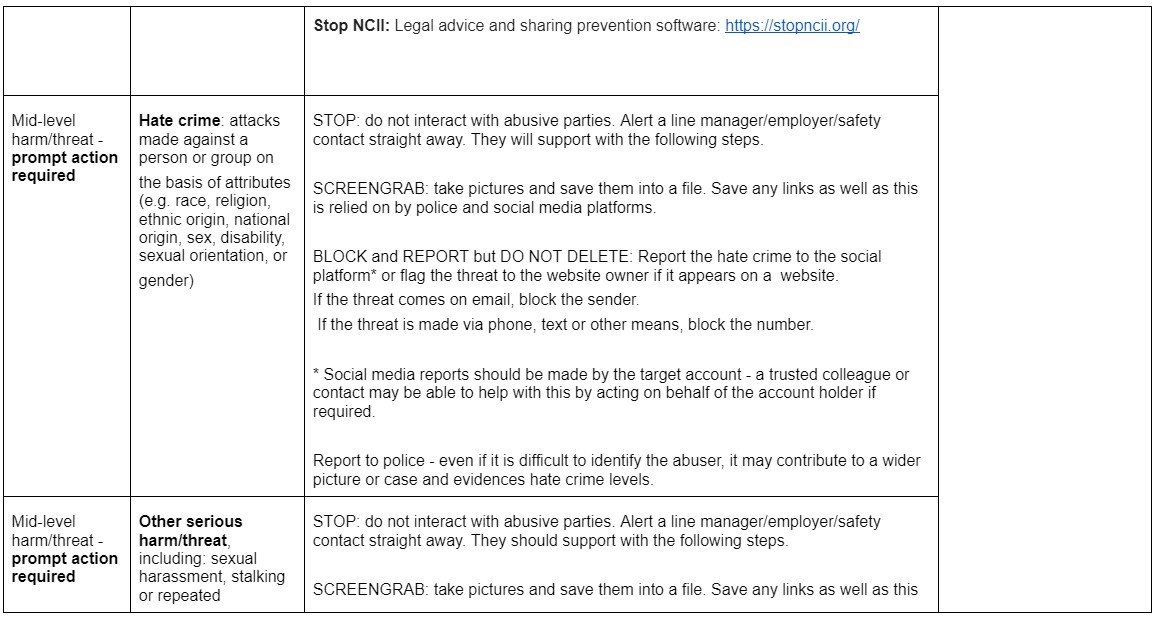
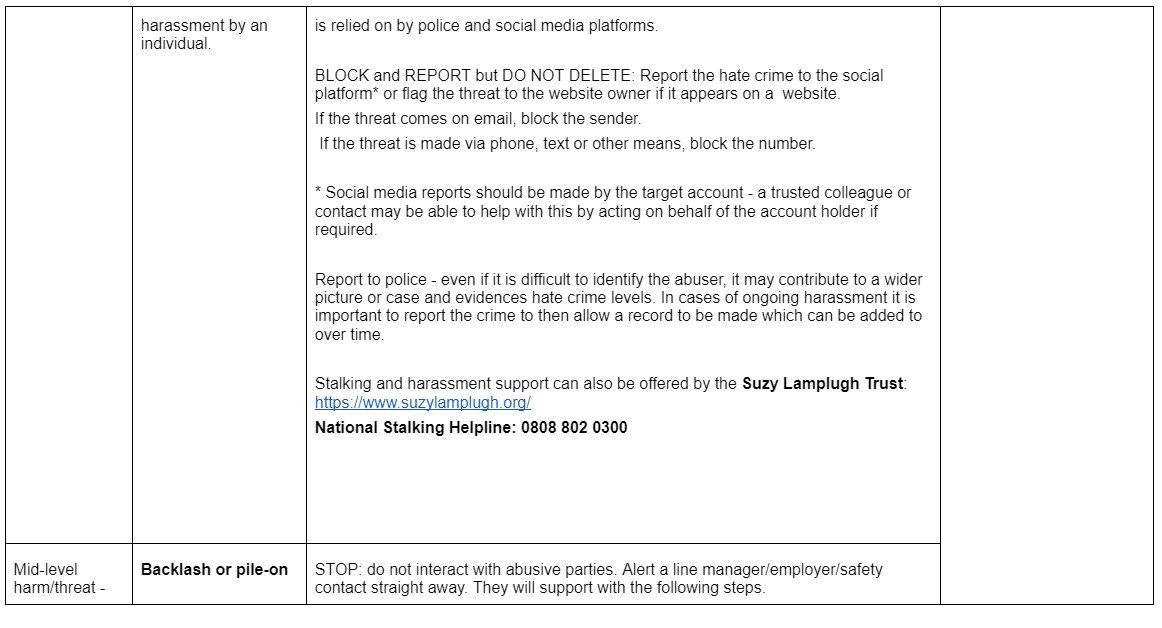
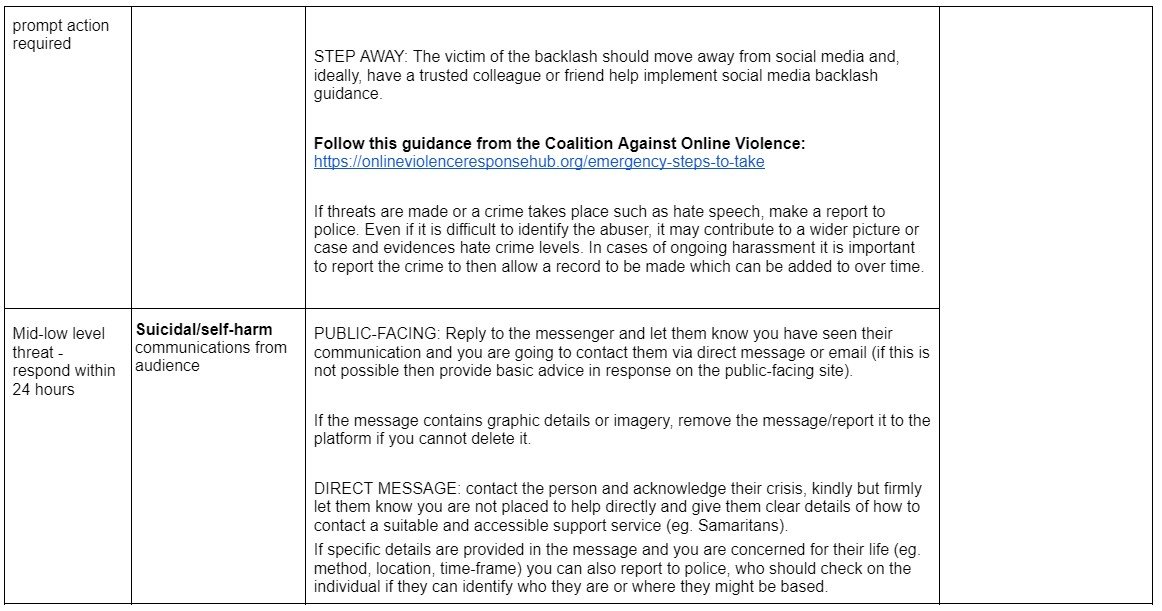
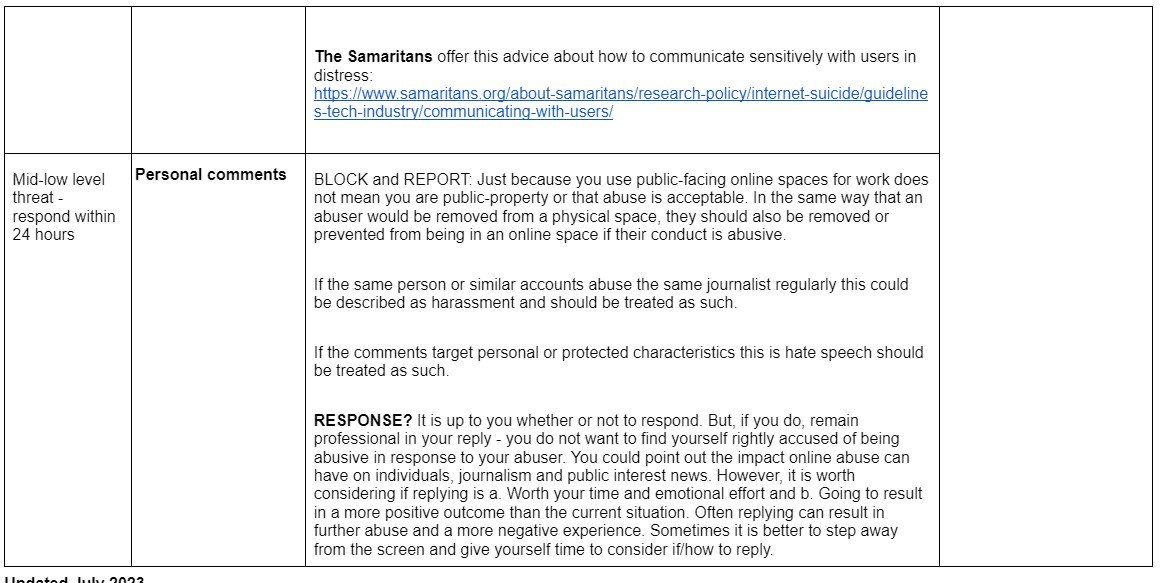
The grid below offers guidance around immediate response to secure online, physical, digital and psychological safety. The right-hand column offers follow-up services/support that should be considered.
Ideally the actions in the immediate procedure should be supported by a manager or colleague to assist the target with securing their safety without being exposed to the online harm.